July 16, 2025
How Role-Based Access Control Works in Practice
Why Role-Based Access Control is Critical for Australian Businesses in 2025
How Role-Based Access Control Fits into a Broader Security Strategy
How To Correctly Setup Role-Based Access Control For Your Business
Role-Based Access Control (RBAC) is a security model and framework that helps businesses manage who can access systems, applications, and data, based on clearly defined roles within the business.
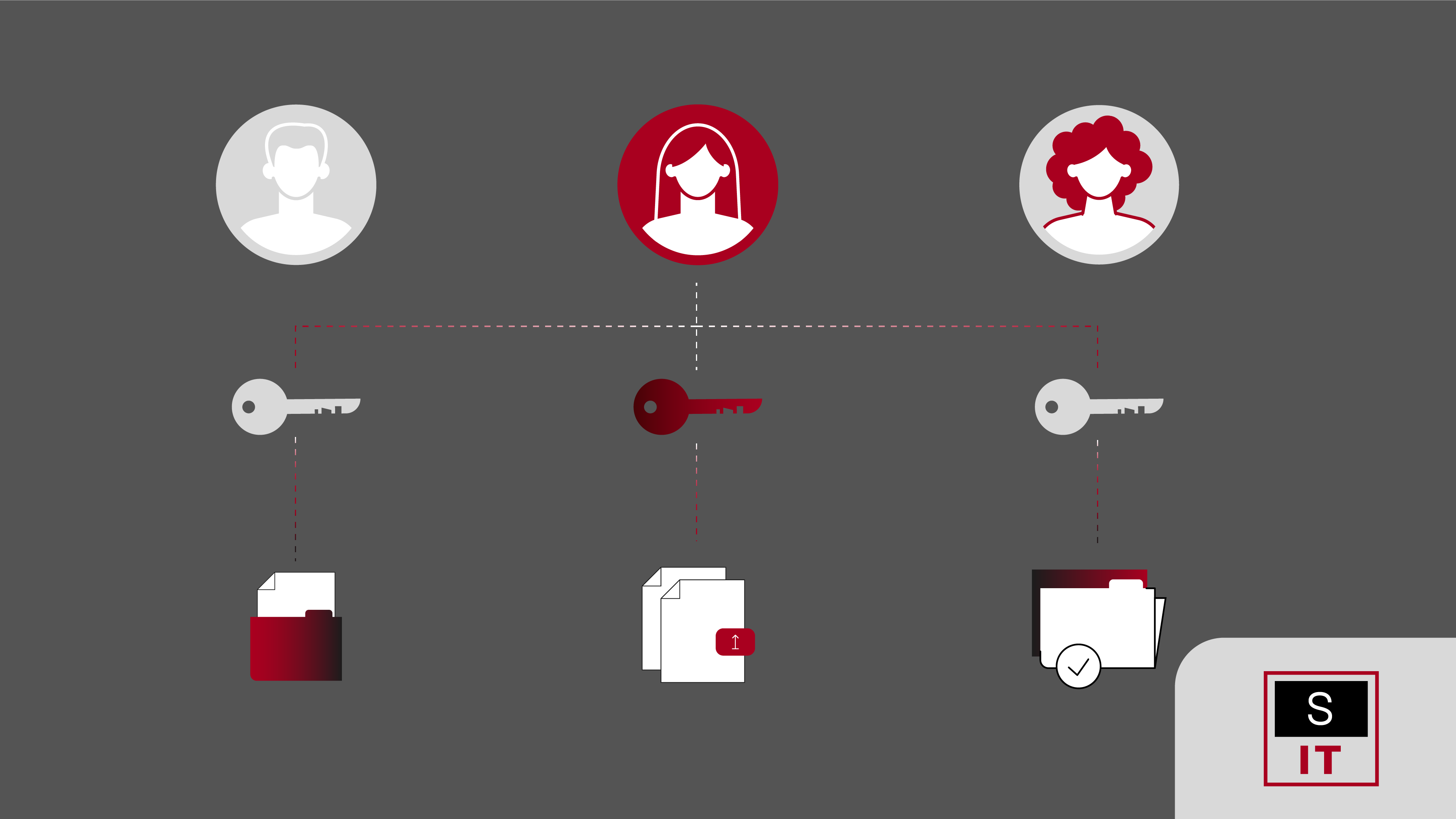
Role-Based Access Control assigns permissions to roles rather than individual users. A role represents a set of responsibilities, such as Finance Manager, HR Administrator, or IT Support. Users are then assigned to these roles, automatically inheriting the permissions needed to do their jobs and nothing more.
This approach reduces the risk of accidental or unauthorised access by ensuring employees can only see or modify information relevant to their duties. RBAC is a cornerstone of security best practice, helping businesses maintain accountability, enforce least privilege, and demonstrate compliance.
RBAC operates on a simple principle: access is granted according to role membership, not ad hoc decisions. When a new employee joins, they are assigned to the appropriate role, which defines exactly what they can access across systems and data.
Role-Based Access Control involves three main components:
For example, in a finance department:
When the role is updated, the permissions automatically apply to all users in that role, streamlining access management as teams grow or change. RBAC systems can also enforce separation of duties. For instance, the person entering invoices cannot approve them, reducing the risk of fraud or error.
Platforms such as Microsoft Entra and Okta provide tools to create roles, assign permissions, and generate access reports across cloud and on-premises systems.
In practice:
Today’s operating environment is more complex than ever. Remote work, cloud platforms, and interconnected systems increase the risk of unauthorised access if permissions are not carefully managed.
One key driver for RBAC adoption is compliance. The Cyber Security Act 2024 and frameworks like ISO 27001 require businesses to demonstrate clear access controls and maintain evidence that only authorised individuals have access to specific systems and data. Role-Based Access Control simplifies this by aligning permissions with defined job functions rather than managing each user’s access manually. This approach not only makes audits more straightforward but also supports ongoing compliance by providing an auditable record of who had access to what, and when.
User error is another leading cause of breaches. For example, granting blanket access to new employees, overlooking excessive permissions when someone moves departments, or failing to revoke access for departing employees increases the risk of data leaks or misuse. RBAC helps reduce this exposure by automating permissions management based on roles rather than individuals. When someone leaves, changing their role or removing them from the system automatically strips their access rights across all connected applications and resources. This reduces reliance on manual updates and ensures your environment remains secure even during employment changes.
RBAC works best as part of a layered approach to security and governance. On its own, it does not prevent every threat, but it significantly reduces the attack surface and supports the principle of least privilege.
Consider these examples:
DefenderSuite Plans are particularly valuable in sectors such as finance, healthcare, legal, and education, where strict access controls are mandatory. However, any business can benefit from RBAC by reducing manual effort and supporting consistent security.
Many platforms already include RBAC capabilities. Microsoft Entra integrates with Microsoft Azure and Microsoft 365 to centralise identity and access management. However, successful RBAC requires more than turning on default settings. DefenderSuite extends these tools with advanced policies, monitoring, and reporting tailored to your needs.
To make RBAC effective, your business should:
DefenderSuite helps you implement Role Based Access Control confidently, ensuring your controls are robust, compliant, and efficient.
Superior IT helps Australian businesses protect critical systems and data by designing and configuring Role-Based Access Control strategies aligned to your operational and compliance requirements.
Call Us to Get Started: 1300 93 77 49
Email: info@superiorit.com.au
Website: www.superiorit.com.au
Australian Government Department of Home Affairs. Cyber Security Act 2024. Available from: https://www.homeaffairs.gov.au/cyber-security-subsite/Pages/cyber-security-act.aspx
Microsoft. Microsoft Entra Identity and Access Management. Available from: https://www.microsoft.com/en-au/security/business/identity-access/microsoft-entra
Okta. Access Management Overview. Available from: https://www.okta.com/products/access-management/
If you're looking for more info or assistance, we're a call, email or message away.
App Development, Business & Tax, and Digital Marketing. Super Charge Your Growth.
Existing Customer Support Portal, speak to one of our experts in no time.