
July 29, 2025
Why You Should Review Audit Logs in Microsoft 365
How to Set Up Audit Logs in Microsoft 365
How to Check Microsoft 365 Access Logs
Microsoft 365 Audit Logs are detailed records that capture nearly every action users and administrators take across your cloud environment. Every time someone signs in, accesses a file, shares a document, changes permissions, or modifies settings, that event is logged.
These records form a complete timeline of user activity and administrative operations, giving your business the visibility needed to protect data and maintain compliance.
Audit logs are essential tools for IT administrators, compliance officers, and Managed Service Providers (MSPs). They rely on this data to monitor behaviour, identify security threats, and prove adherence to regulatory requirements.
Without audit logs in place, your business loses critical insight into how data is accessed and used. This lack of visibility makes it difficult to detect unauthorised activity, investigate incidents, or confirm that policies are being followed.
For businesses, the benefits of audit logs are substantial. They enable you to:
Audit logging is included in most Microsoft 365 enterprise plans, such as E1, E3, and E5.
If your organisation uses Microsoft Teams, SharePoint Online or OneDrive, you can collect and analyse audit data across all these services through the **Microsoft Purview Portal under**
This centralised approach ensures your business maintains control and accountability across the entire Microsoft 365 environment.
Audit logs in Microsoft 365 record detailed events such as sign-ins, file access, edits, deletions, sharing activity, and administrative changes. This data is essential for several reasons:
Consistent auditing strengthens your ability to detect problems early, enforce policies, and protect your business’s reputation.
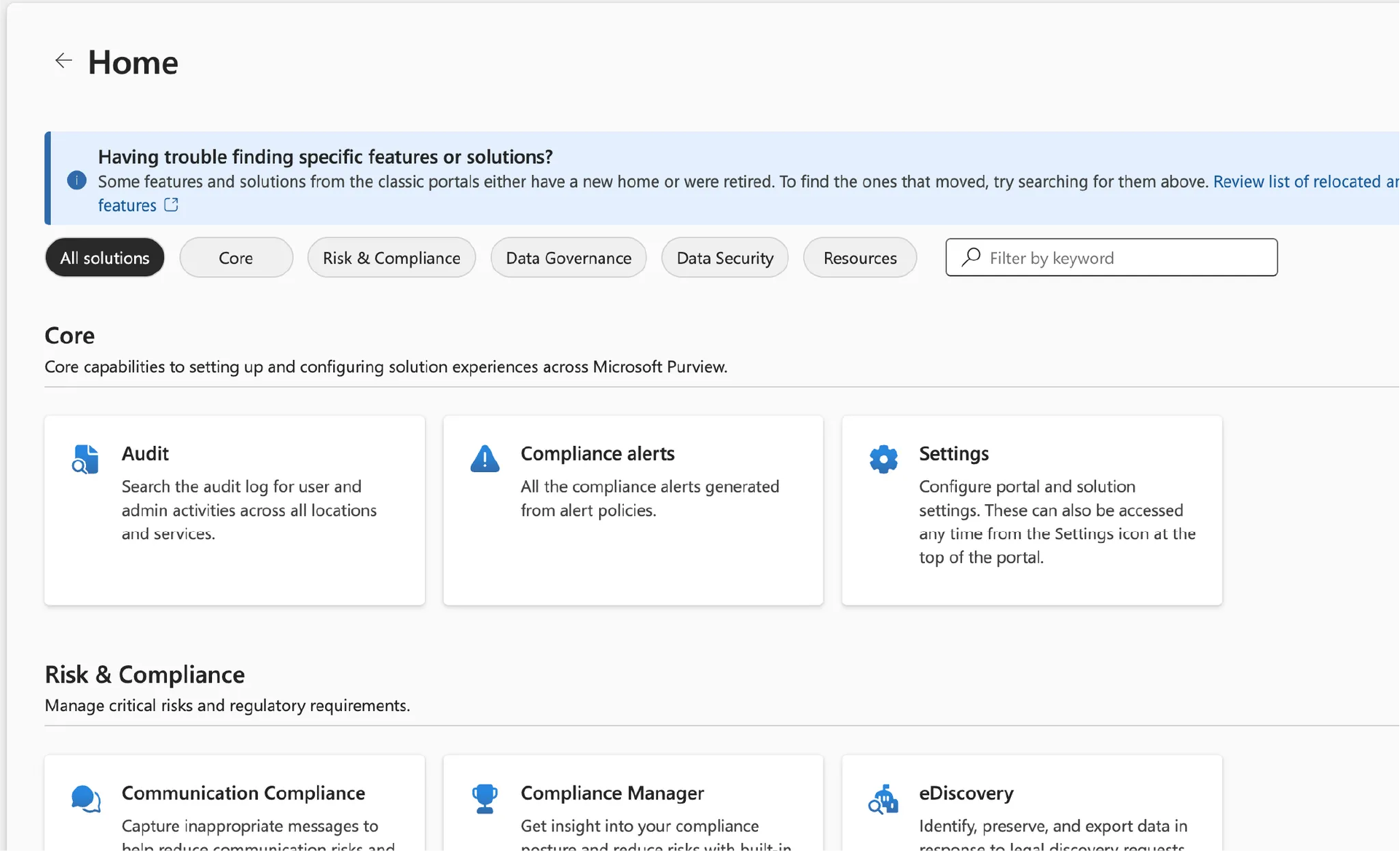
Setting up audit logging is a straightforward process, but you need the right plan and permissions. Here is how to get started:
1. Check Your Subscription:
For Audit (Standard) features, users must have a Microsoft 365 Business, or Office 365 Enterprise, or Microsoft 365 Enterprise license.
For Audit (Premium) features, users must have either a Microsoft 365 E5 license, or a Microsoft 365 E3 or Office 365 E3 license with a Microsoft 365 E5 Compliance or Microsoft 365 E5 eDiscovery and Audit add-on license.
If you don't have an existing Enterprise E5 plan and want to try these Audit (Premium) features, you can start a free 90-day Microsoft Purview solutions trial.
2. Enable Audit Logging:
In many cases, auditing is enabled by default. To verify, sign in to the Microsoft Purview portal at https://purview.microsoft.com/home
In the navigation pane, select Audit. If you see a prompt to turn on auditing, follow the instructions to enable it. It can take a few hours before logs start collecting.
3. Understand the Apps Involved:
Audit logs cover activities in Exchange Online, SharePoint Online, OneDrive for Business, Teams, and more. Be aware that some services record different levels of detail.
4. Get Set Up with Superior IT:
If you prefer to have expert support, Superior IT can configure audit policies, retention settings, and alert rules tailored to your business. Our team ensures your environment records the right events and keeps them for as long as needed.
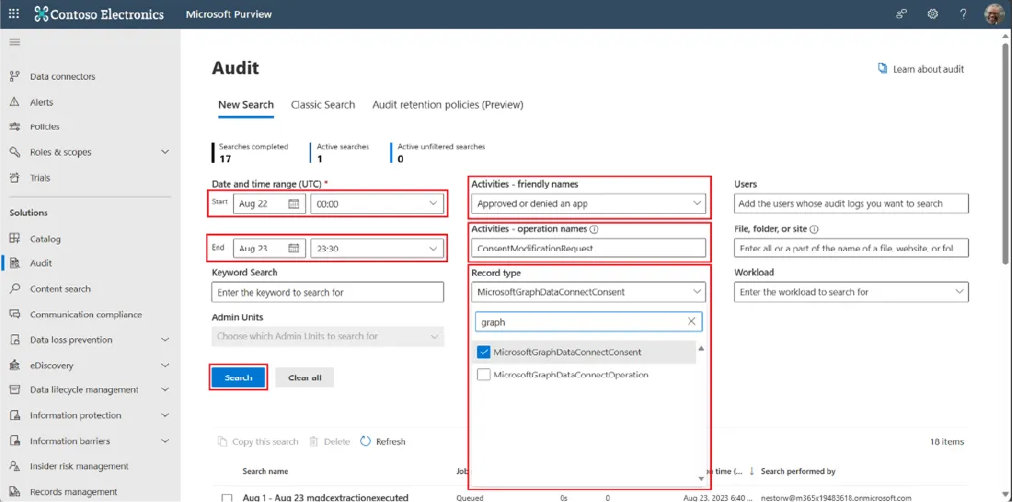
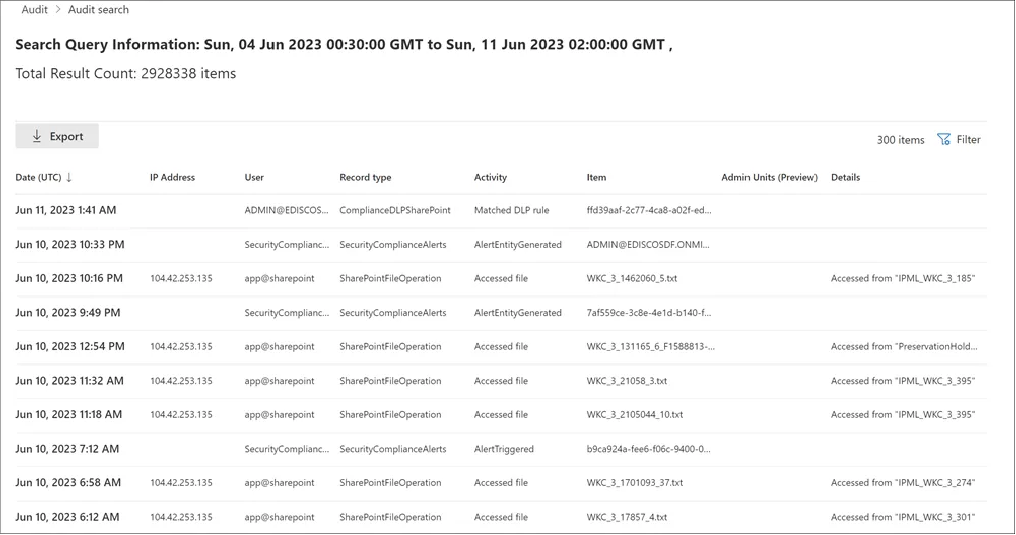
Once your audit logs are active, you can search and review them as needed. Here is the process step by step:
For example, to see all file deletions by a specific user in the last month, select the “Deleted file” activity, enter their username, and set your date range.
With DefenderSuite Plans, you can activate extended retention and more granular auditing, including detailed file and mailbox access records beyond the default retention period.
Checking audit logs should be part of a routine security process. Pairing audit reviews with clear access policies, user training, and layered protections ensures your environment remains secure.
DefenderSuite Plans provide the structure you need to oversee activity, respond to incidents, and maintain visibility across Microsoft 365. With dedicated Microsoft 365 Managed Security and Data Loss Prevention (DLP), DefenderSuite helps your business monitor user actions, secure sensitive information, and reduce the risk of data breaches.
Partnering with a managed service provider (MSP) offers significant advantages over managing security alone. An MSP brings specialist expertise, proven processes, and the capacity to continuously track and respond to threats in real time. Rather than relying on limited internal resources, your business benefits from proactive monitoring, detailed reporting, and tailored controls that align with compliance requirements and your specific risk profile.
Regular monitoring helps you detect and investigate issues before they escalate, protect confidential data, and demonstrate a mature security posture to clients and regulators.
By combining DefenderSuite with your internal policies and training, you maintain control over your environment without placing an unrealistic burden on your internal teams.
Superior IT helps Australian businesses protect critical systems and data by designing and configuring Role-Based Access Control strategies aligned to your operational and compliance requirements.
Call Us to Get Started: 1300 93 77 49
Email: info@superiorit.com.au
Website: www.superiorit.com.au
Microsoft. Search the audit log in Microsoft Purview. Microsoft Learn.
Microsoft. Start a Microsoft Purview trial. Microsoft Learn.
Microsoft. Microsoft Purview Compliance Portal. Microsoft Purview.
If you're looking for more info or assistance, we're a call, email or message away.
App Development, Business & Tax, and Digital Marketing. Super Charge Your Growth.
Existing Customer Support Portal, speak to one of our experts in no time.