August 6, 2025
Why Streamlined Off-boarding Matters
How to Fully Revoke Microsoft 365 Access
In any business, there are times when access to systems must be revoked immediately and completely. This could be due to a resignation, role change, termination, or contractor off-boarding. It may also follow an incident involving policy breaches or suspicious activity. Fast, precise off-boarding is especially important when the departing user had elevated permissions, admin access, or handled sensitive data.
When the off-boarding process is rushed or poorly managed, businesses can encounter serious issues. For example:
A comprehensive access revocation process reduces these risks, ensures continuity for the business, and supports audit-readiness.
User accounts that remain active or are only partially revoked pose a direct threat to business systems. Even if the user no longer has a workstation or active licence, cached sessions and indirect permissions can still provide access to company data.
Key concerns include:
While many businesses also use non-Microsoft platforms, this guide focuses specifically on managing off-boarding within the Microsoft 365 environment, where centralised controls can significantly reduce security and operational risk.
Microsoft 365 simplifies this process by consolidating identity, access, storage, and communication into a single administrative platform.
With tools like Microsoft Entra ID, teams can centralise user management, track permissions across services, and execute revocation actions in one place. This integration reduces the complexity of managing multiple systems and makes it easier to ensure no access points are left behind.
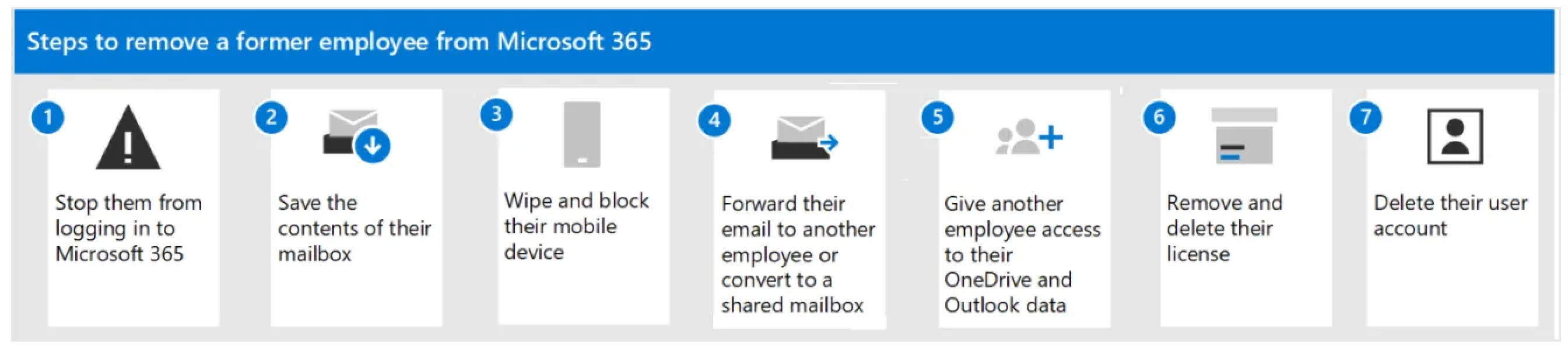
Follow these steps to fully revoke user access within the Microsoft 365 environment. This ensures all active sessions are terminated, services are disconnected, and no residual permissions remain.
Go to the Microsoft 365 Admin Center and sign in using an account with the Global Administrator or User Management Administrator role. This portal allows centralised management of users, licences, and services.
In the left-hand navigation menu, go to Users > Active users. Use the search bar to find the user by name or email address. Click the user’s name to open their account page.
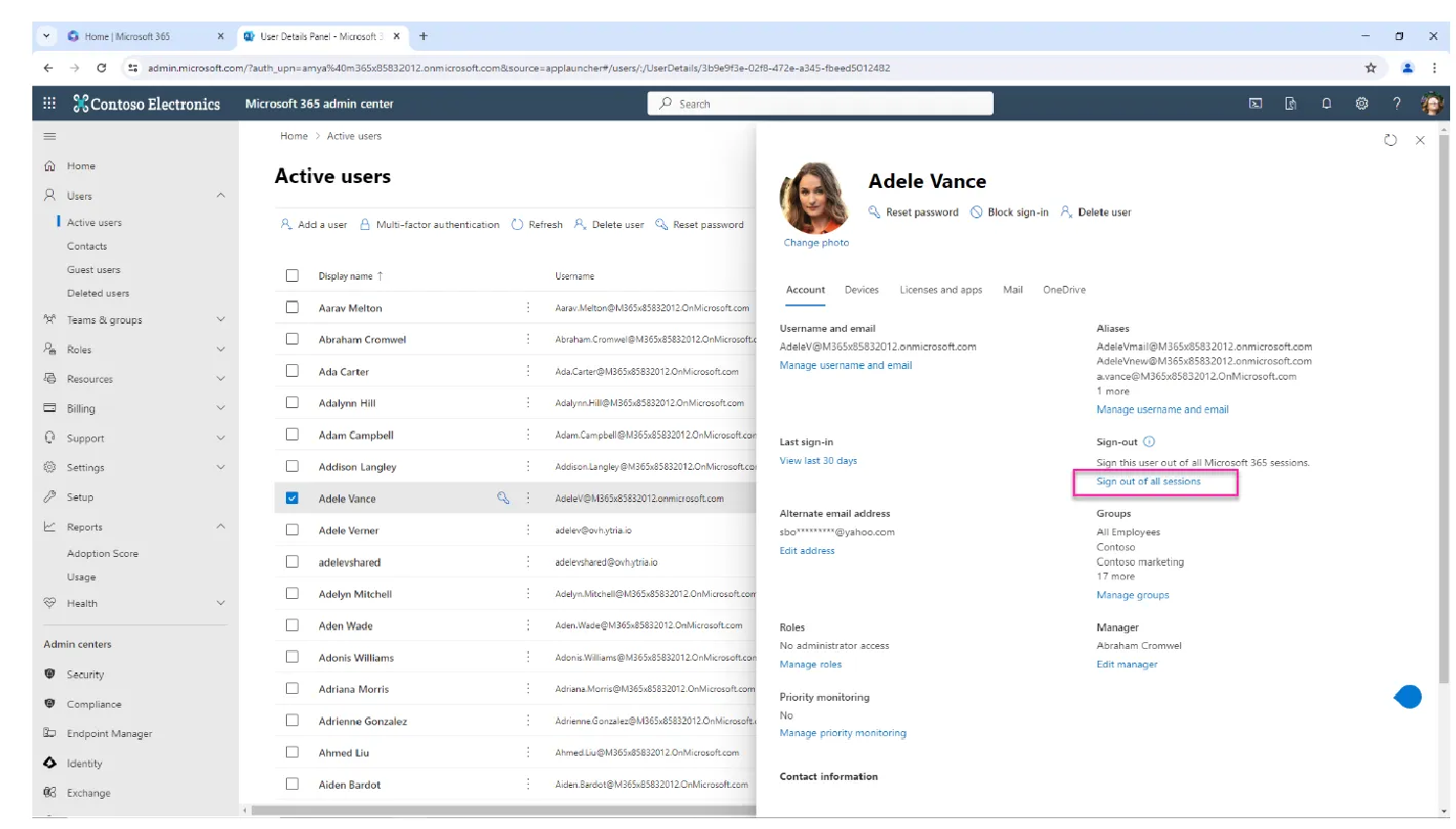
On the user’s profile page, click Block sign-in. Confirm the action when prompted. This prevents the user from accessing all Microsoft 365 services, including web and desktop apps for Outlook, OneDrive, SharePoint, and Microsoft Teams.
In the One-time sign-in links and password reset section, choose Sign out of all sessions to invalidate any current access tokens across devices.
Then select Reset password if the account will be repurposed. Make sure credentials are sent to another administrator, not the user.
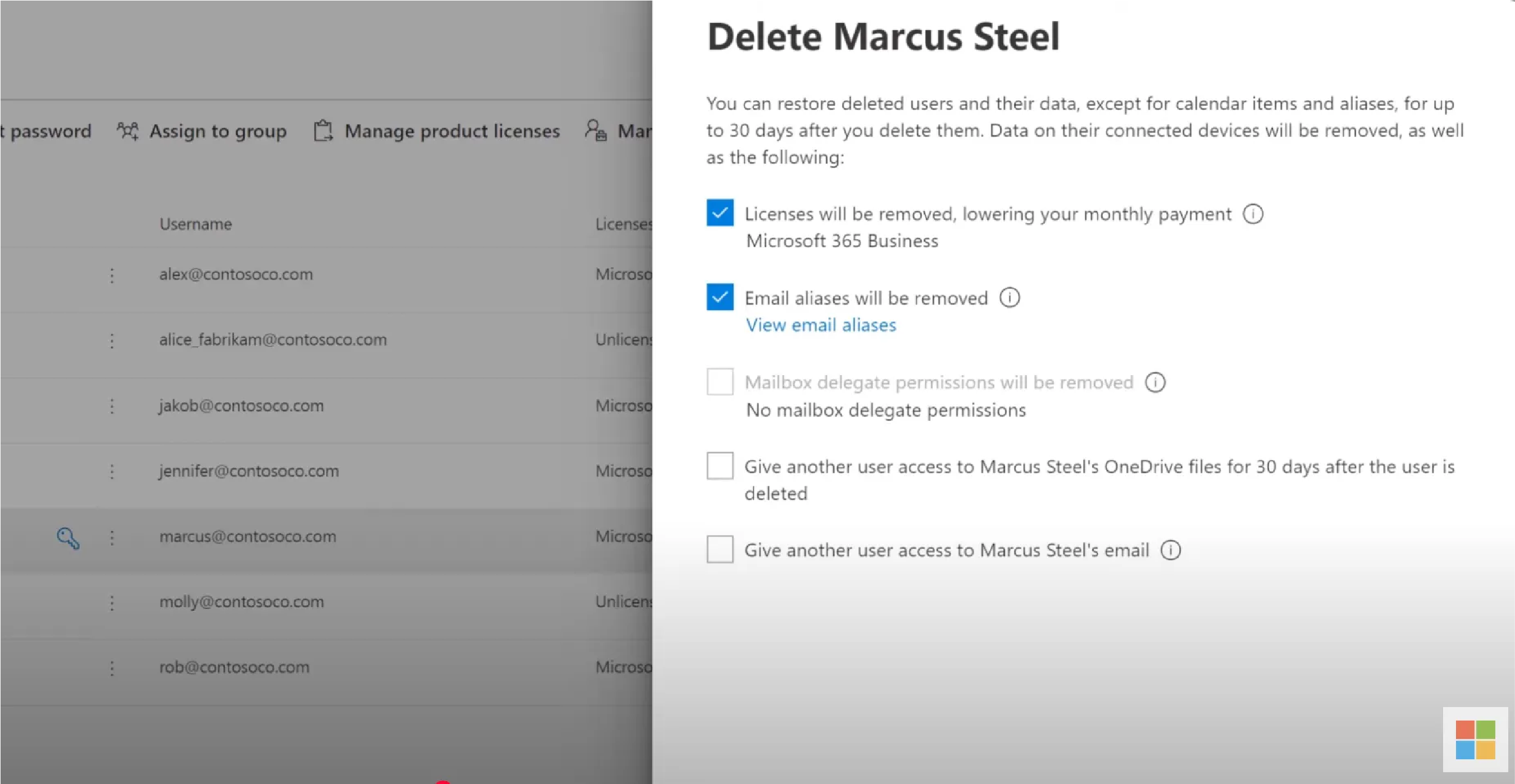
Select Licenses and Apps from the user profile panel. Uncheck all assigned licences (e.g. Microsoft 365 Business Premium, Microsoft 365 E3, etc.). This disables the user’s access to services like Exchange Online, Microsoft Teams, and Office apps, and frees the licence for reassignment.
Revoking access through the Microsoft 365 Admin Center blocks sign-in, signs out active sessions, and removes assigned licences. However, it does not automatically remove the user from roles, group memberships, or delegated access across services.
To fully secure the account, you must manually review and remove the user from any:
These indirect access paths remain active unless explicitly revoked. After cleanup, you can verify deactivation by checking user activity through Microsoft Purview Audit. This confirms the account is no longer in use across the Microsoft 365 environment.
Learn how to Revoke User Access or Deleting a User from Microsoft’s video guide.
Ad hoc user off-boarding introduces risk. A structured, repeatable process ensures that no steps are missed and that the business retains control over digital assets and administrative privileges.
A well-managed off-boarding process will:
Structured off-boarding helps businesses maintain continuity, reduce user error, and remain compliant with data protection requirements.
With DefenderSuite Plans, complete off-boarding workflows is backed by real-time monitoring and secure access policies.
Our team ensures that no account is left active, no role is forgotten, and no data is exposed. Whether managing one user or an entire department, DefenderSuite supports secure, efficient transitions.
Superior IT provides structured access control services and secure off-boarding solutions for Australian businesses. If you need to revoke access, transfer data, or manage complex user permissions, our team is ready to assist.
Call: 1300 93 77 49
Email: info@superiorit.com.au
Visit: www.superiorit.com.au
Microsoft 365 Help for Small Businesses. How to remove access to Microsoft 365 for a terminated employee (Video)
Microsoft. Revoke user access in Microsoft Entra ID
Microsoft. Remove a former employee from Microsoft 365
If you're looking for more info or assistance, we're a call, email or message away.
App Development, Business & Tax, and Digital Marketing. Super Charge Your Growth.
Existing Customer Support Portal, speak to one of our experts in no time.